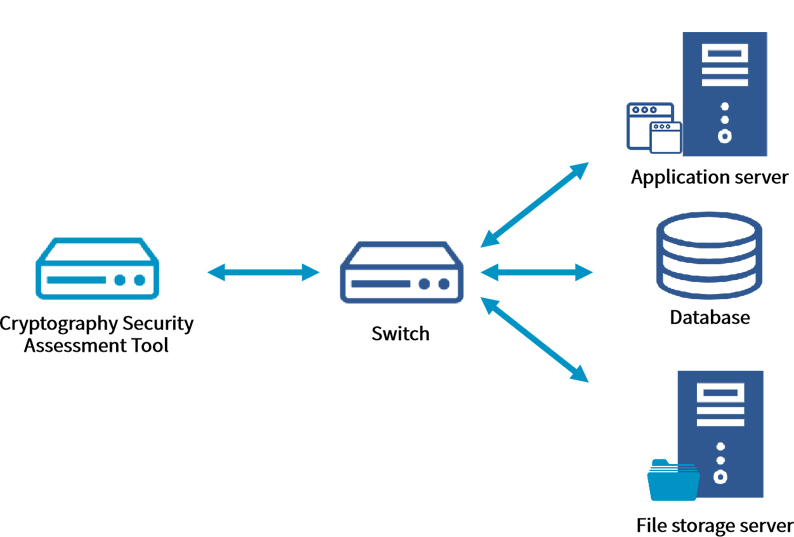
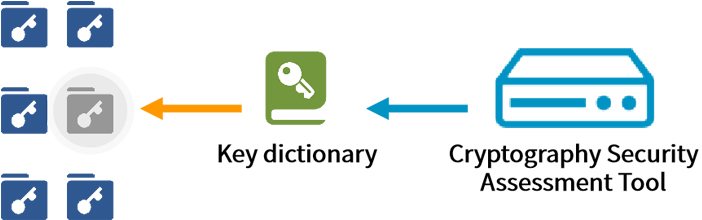
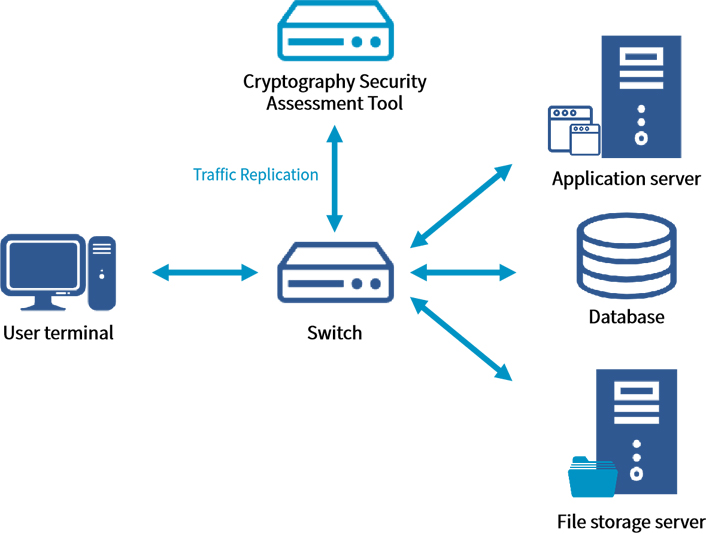
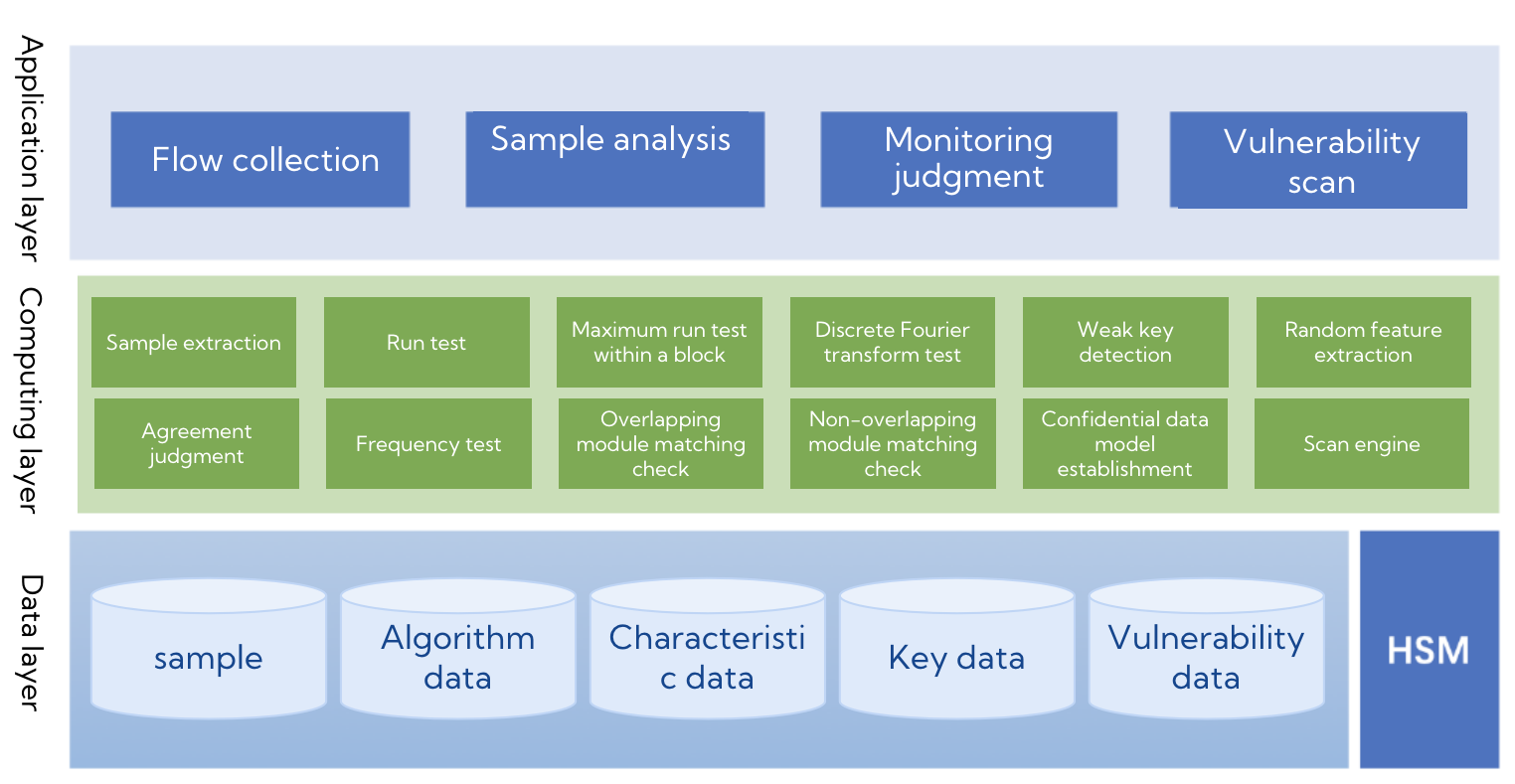
Cryptography Security Assessment Toolbox implements the content required in cryptography security assessment test as a tool to assist the agency evaluation and enterprise self-evaluation. It supports access to the target environment by bypass deployment. Through the functions and methods of collecting sample data, ciphertext analysis, and cryptographic algorithm restoration, it can quickly determine whether the target system uses cipher, whether SM cipher is used, and whether the cryptographic protection mechanism is effective, providing a strong support for the cryptography security assessment test.